Automated Offsite Snapshots
Adding Home Assistant to My Synology/Dropbox Backup Routine
There was a time when I felt comfortable using GitHub as my main backup solution for Home Assistant. I would backup my secrets.yaml via my workstation backup routine (on the rare times that it changed) and I considered the database to be expendable. As Add-Ons have started becoming commonplace and various components have started moving from yaml to integrations I no longer consider this sufficient.
This solution utilizes the Remote Backup addon, my home Synology Diskstation NAS and Dropbox via encrypted Hyper Backup tasks.
Requirements
Durability
We’ve grown fond enough of the system that I consider it worth at least 3-2-1 for its backups. The chances of meaningful loss with this configuration is very low.
- 3+ copies
- Running in HASS
- Snapshots
- Previous 3 daily snapshots in Home Assistant
- Previous 14 daily snapshots (above included) in NAS
- Backed up to Dropbox
- Encrypted, versioned, and non-public via Hyperbackup
- 2+ Media
- Micro-SD (in my Pi)
- SATA Hard Drive (in my NAS)
- Dropbox
- 1 copy offsite
- See also: Dropbox
Obviously my configs are also still in github, further minimizing risk.
I want the HASS part to be self contained
If we need to restore from backup, that restore should be everything needed to be up and running again - including the backup routine. To this end I am going to use Hass.io snapshots, the Hass.io remote backup plugin, and vanilla Home Assistant automations.
Database Too
It’s not expendable anymore but also not… mission critical (yet). I am not doing 3-2-1 here but I am doing a daily offsite backup.
Prerequisites
- The Home Assistant device and the Synology Diskstation have network routes and access controls that allow SSH traffic.
- Hypervisor is set up on the Synology Diskstation and configured to use Dropbox.
- There should be a backup folder in the main volume of the Synology with a home assistant subfolder.
/volume1/Backups/HomeAssistant/
Set up
Generate A Key Pair
A public/private keypair is needed for the remote backup addon (it’s also just a good idea). This is best done (saved and securely backed up) somewhere other than the synology.
ssh-keygen -t rsa -b 4096 -C "hass_backup"
I used my workstation; saving them in a backed up directory and in my password manager.
Synology User
- From The Users section of the DSM Control Panel select Create
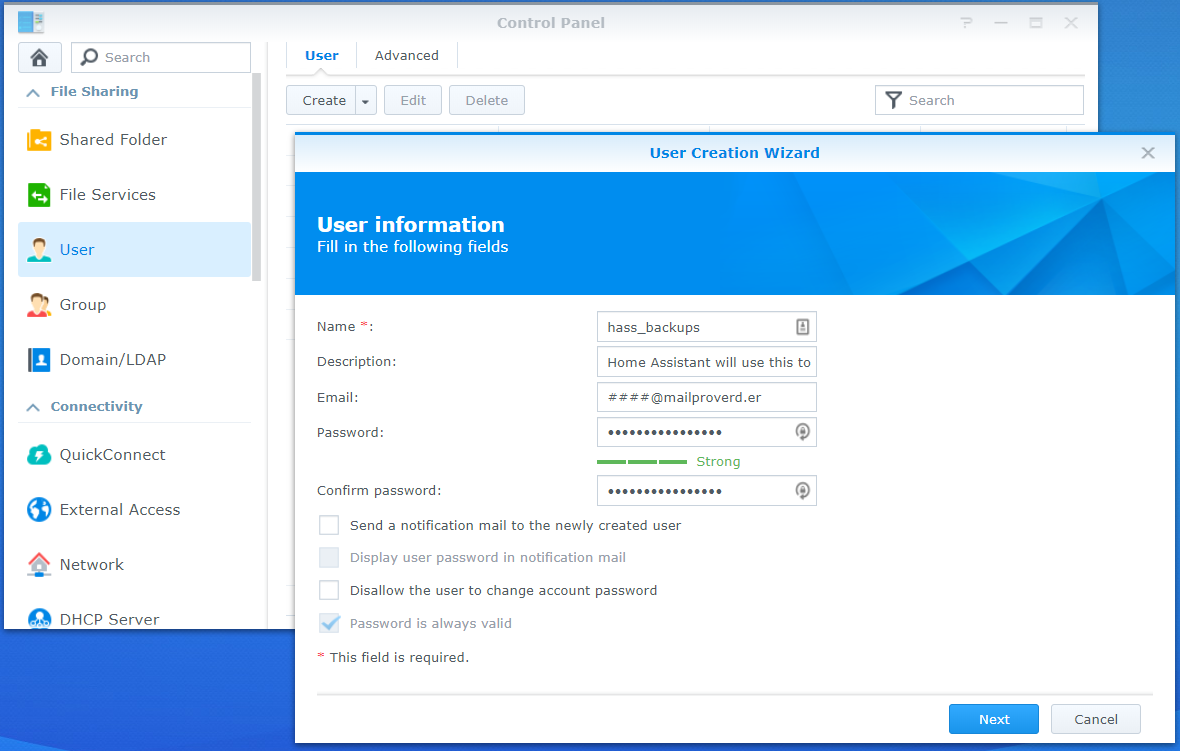
- Make sure the user is in the admin group. As of the time of this writing only admin users are allowed SSH.
- The user should only be given access to two folders: the one where backups are being sent (
volume1/Backups/HomeAssistant) and thehomesdirectory. If the homes directory doesn’t exist it will be created in a later step then it can be given read/write access here.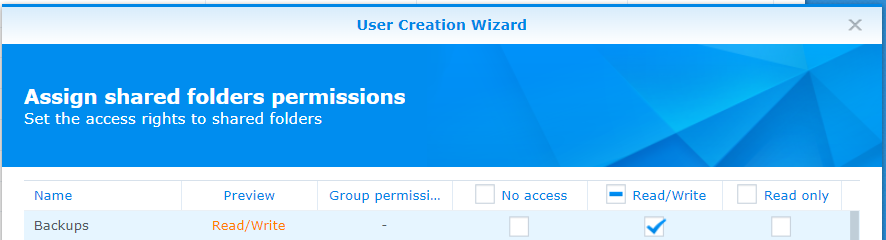
- Deny all access to applications
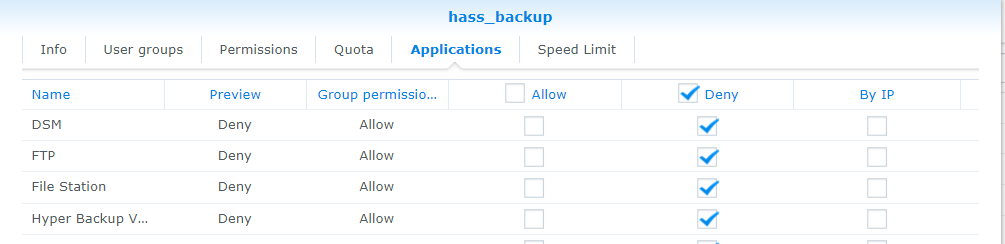
Synology SSH/SCP
- If SSH isn’t otherwise on it needs to be enabled.
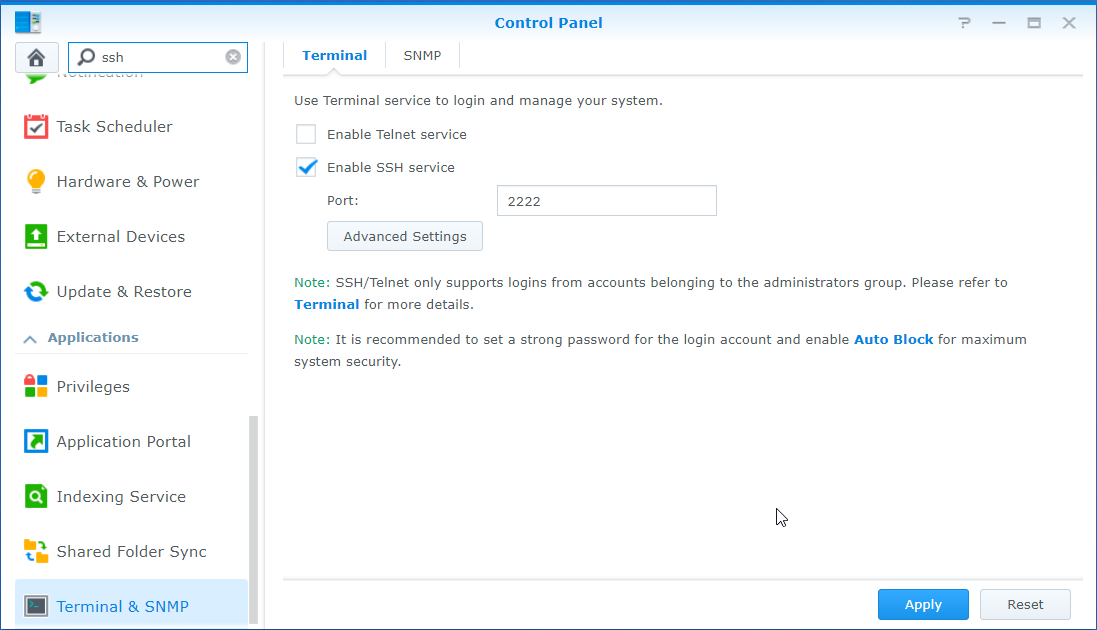
- Make note of the port.
- In the advanced tab of the Users section of the control panel, scroll to the bottom and enable home directories.
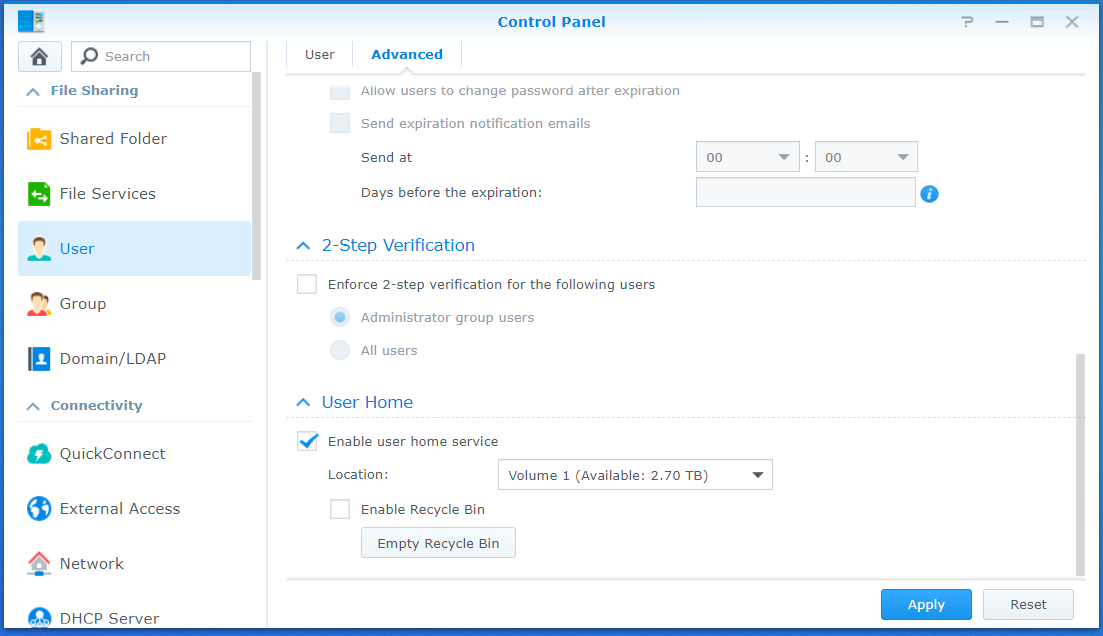
- If the user home directories weren’t previously enabled remember to give the
hass_backupuser read/write permissions in the Synology DSM User Control Panel.
- If the user home directories weren’t previously enabled remember to give the
- Change the home directory in
/etc/passwdto be thehomesdirectory that the Synology created when home directories were enabled. SSHing in using the synology user is now possible, but there will be an error about not being able chdir into your home directory. This error won’t prevent fixing of the problem.sudo vim /etc/passwd- Change
/var/services/homes/hass_backupto/volume1/homes/hass_backup - I suspect this would be unnecessary if I had enabled home directories before enabling SSH or creating the hass_backup user but I was disinclined to go back and unwind everything to find out.
- Change
chmod 0750 /volume1/homes/hass_backup- At this point it should be possible to ssh into the synology using the hass_backup user’s password (without any errors).
ssh hass_backup@<synology ip address>:2222
Enable Public Key Authentication
While logged into the Synology via SSH:
sudo vim /etc/ssh/sshd_config- Uncomment these 3 lines
#RSAAuthentication yes #PubkeyAuthentication yes #AuthorizedKeysFile .ssh/authorized_keys - Restart the ssh service
sudo synoservicectl --reload sshd mkdir ~/.sshchmod 0750 ~/.sshvim ~/.ssh/authorized_keys- Paste the contents of the public key generate above into a new line of this file.
- At this point it should be possible to ssh into the synology without entering a password.
ssh -i <location of private key> hass_backup@<synology ip address>:2222
Hass.io remote backup plugin
- Add the repository and install the add-on per its instructions.
- Configure it with the everything that was just set up.
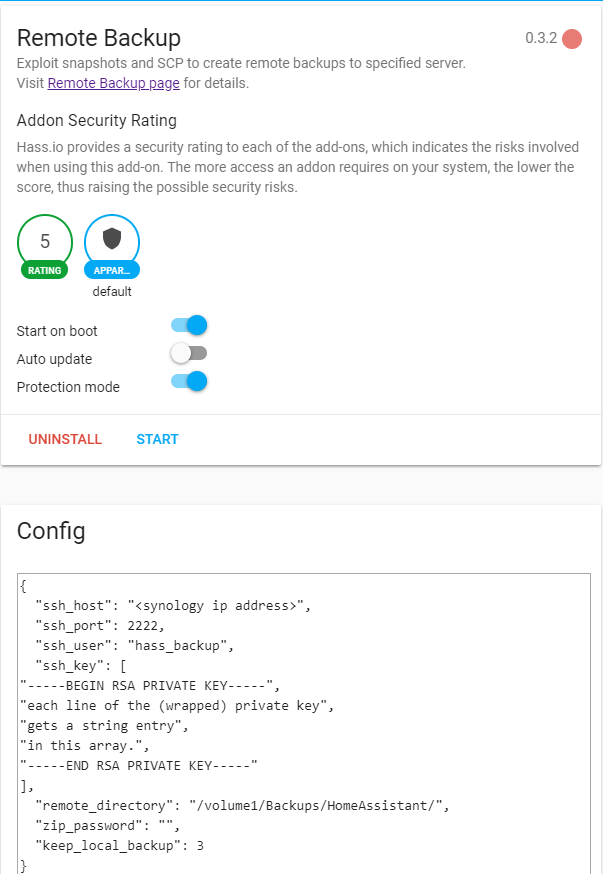
At this point it should be able to test that backups are being sent to the Synology via the Developer Tools Service panel. It will take a few minutes to perform the backup after the service call is made.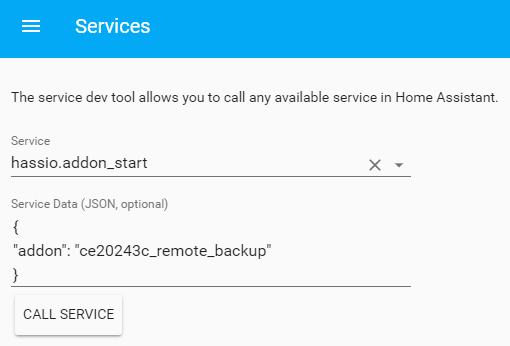
Automation
This automation is taken directly from the remote backup add-on docs. The time was changed and the id was added.
- id: daily-backup
alias: Daily Backup at 00:30
trigger:
platform: time
at: '00:30:00'
action:
- service: hassio.addon_start
data:
addon: 954f2f4e_remote_backup
Hyper Backup
The hyper backup job is pretty simple. Backup the HomeAssistant folder and the MariaDB application (which at the time of this writing is only used by Home Assistant).
- Create a new “data backup task” with Dropbox as its destination.
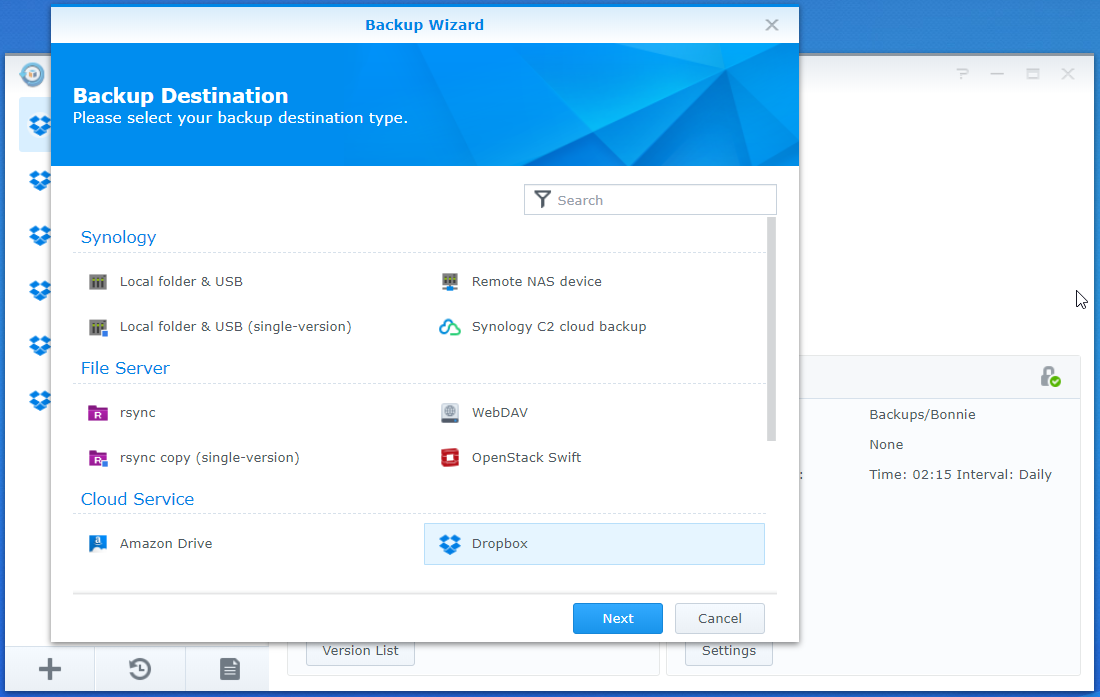
- A new browser window will open to grant Hyper Backup dropbox permissions. Allow them.
- Select the Dropbox folder to send to (
SynoBackups) and what the and what to call within that folder (HomeAssistant).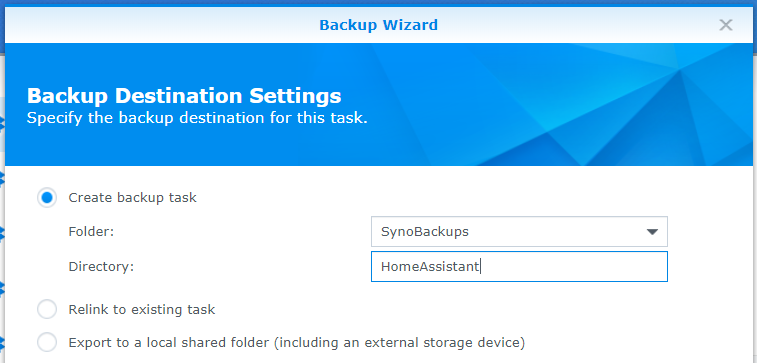
- Select the Synology folder to back up from the “Data Backup” screen.
Backups > HomeAssistant - Select the MariaDB 10 from the “Application Backup” screen.
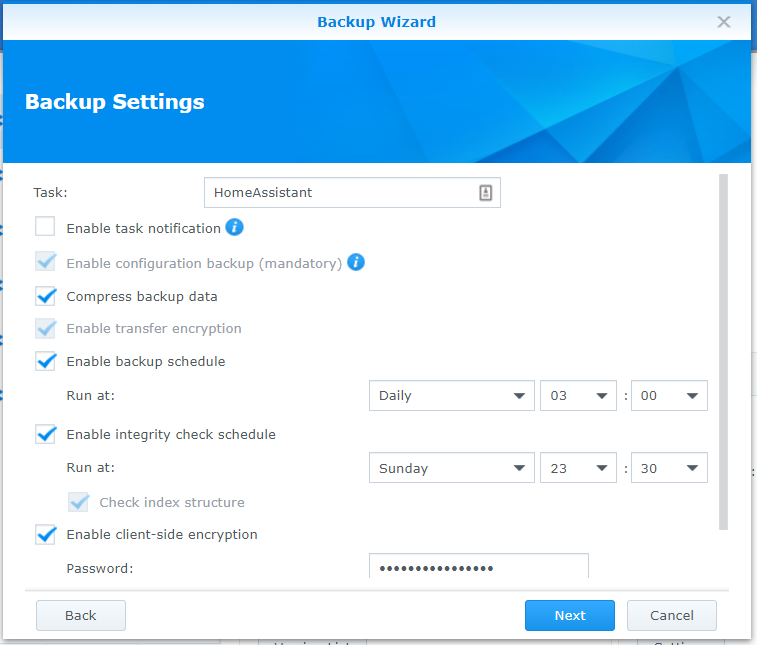
- Set the backup task settings.

- The password for this backup is stored in my password manager.
- At the end of the wizard you will be prompted to have the backup’s encryption key. The backup can be accessed using either the password or the key. If both are kept safe then at lest one should be available when needed.
- I chose a Hyper Backup time sufficiently after my Home Assistant backup automation.
- Choose a rotation schedule. I keep a smart rotation with 128 versions.
- At the end of the wizard, after saving the backup’s encryption key, there is an option to back up now.
- This will be the last thing to test.
- Note: Backing up Maria DB will make it briefly unavailable.
Clean Up
My snapshots are only about 50M, but I still don’t have a reason to keep them all. I am going to prune all local backups older than 14 days.
- Create a User Defined Script under Scheduled Tasks
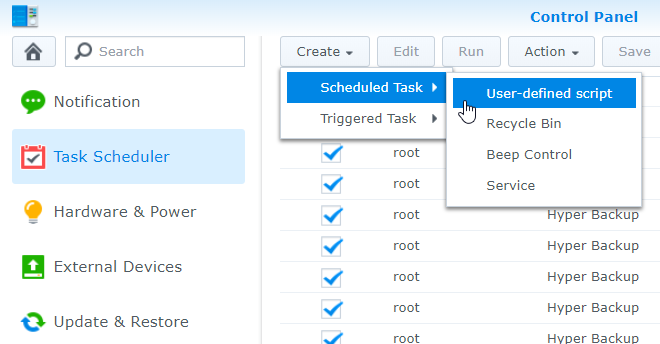
- The task should run as the backup user. Name it descriptively. I set a scheduled task using the administer account but run the task as the hass backup user.
- In the schedule tab choose daily at an time.
- Under task settings set notification settings for abnormal terminations. The script to run is a linux find command with delete flag
cd ~
find /volume1/Backups/HomeAssistant/ -type f -mtime +14 -delete
That change to the home directory at the beginning of this script bypasses a bug currently in syology with non-admin user scripts. Without that the script will throw a permission error.
